Cool PAM with great auditing and easy access to IT assets in the cloud
2019 has been an exciting year for privileged access management (PAM): we’ve seen the rise of the Zero Trust framework, recommendations from Gartner analysts towards Just-In-Time (JIT) and Zero Standing Privileges (ZSP) models and our very own lean PAM - PrivX, has steadily evolved to accelerate the industry’s transition to JIT access.
Also, PrivX project has received funding from the European Union’s Horizon 2020 research and innovation programme under grant agreement No 881221.

Since introducing PrivX in 2018, our aim has been to develop a product that is not only secure, but one that also promotes a positive and practical experience.
Read on to discover how PrivX can bring that experience to your organization, be it in small and medium sized enterprises (SMEs), innovative and cloud-borne R&D teams in large organizations, or early-growth companies.
Always-on logging
Monitor your critical assets with always-on logging to record user activity on every connection established to the asset. Get unimpeachable audit trails with the ability to replay the recorded session, view connection metadata, session-specific audit events and files transferred. There's also keyword search within SSH and SFTP connection transcripts.
Visibility only to authorized resources
Provide customized, manageable and secure access with the need-to-know model, where the identity of all personnel is verified and authorized before granting access to the specific resource.
JIT access with ZSP to cloud & on-prem
Grant one-time access just-in-time (JIT) to only the required target system or application, and ensure that no privileged access exists prior to or after the grant of access has expired. This is what Gartner also recommends with their Zero Standing Privileges approach.
Cut the costs of password vaulting and rotation, and eliminate the need for access key management with ephemeral certificate-based authentication.
Granular access control
Control SSH and RDP traffic by restricting access to specific channels, and limit access to a specific app on your Windows target system when required.
Safe use of shared accounts
Allow safe and audit-able use of shared accounts to access management consoles or target systems without exposing the credentials to the individual users.
Monitor audit events using SIEM & cloud log collectors
Integrate PrivX to your existing monitoring dashboards in external systems such as Splunk, AWS CloudWatch or Azure Event Hub to trigger alerts based on PrivX audit events.
Connect to VPCs securely without additional hardware/software costs
Extend JIT access with ZSP to resources in your Virtual Private Cloud (VPC) using PrivX Extender, an add-on component that proxies connections to target systems at no additional cost.
Native-client friendly
Let your end-users continue using native SSH and RDP clients while retaining all the above benefits of provisioning access via PrivX. Based on the PrivX role assigned to them, they can list the allowed/available targets for a speedy connection authorization.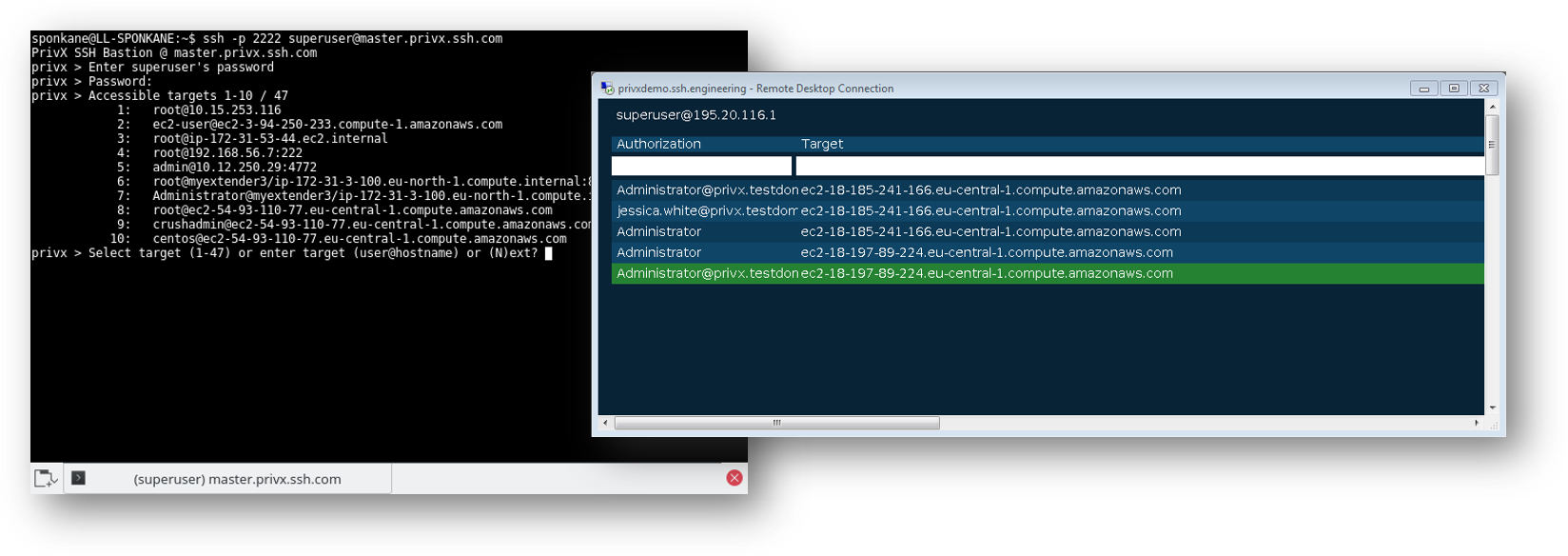
Time to value - One-click, agent-less access to target hosts
Every authorized resource is just one-click away in the PrivX UI with the browser-based SSH & RDP connectivity, along with access to web apps.
With the introduction of a search field in the PrivX home screen, starting connections to authorized resources gets even easier, especially in environments with hundreds or thousands of hosts.
Search within allowed/available targets using protocol, host name, user account or tags and see the status of the service availability right from the search results.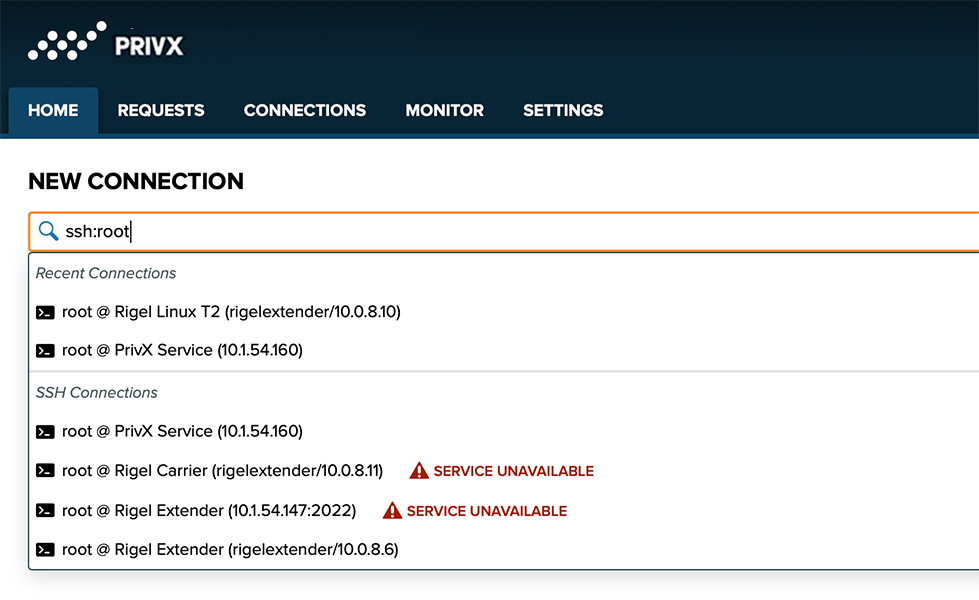
Get the latest PrivX software for free
If you’ve read this far, we’ve likely raised your curiosity about PrivX. So why don’t you take it for a test drive? We offer the full product experience in a browser - with nothing to install - Test Drive Now.
So, will you take the leap towards making security a positive experience for your developers, admins and third parties? We have and we sure hope that you will with the onset of the new year.
Esa Tornikoski
Esa Tornikoski is Product Manager for PrivX and Crypto Auditor products. Esa joined SSH late 2017. Prior SSH he has been working in Product management roles at Telecom and IT security companies (Elisa, F-Secure and Siemens). He has a Master of Science degree in Computer Science from Lappeenranta University of...
